Remote desktop connections , also called RDP for short, are very often used for remote maintenance of Windows systems . This affects private networks as well as company networks.
Today we would like to report on an RDP report and its elimination, which very often occurs in private environments. We have shown you this RDP error message here below.
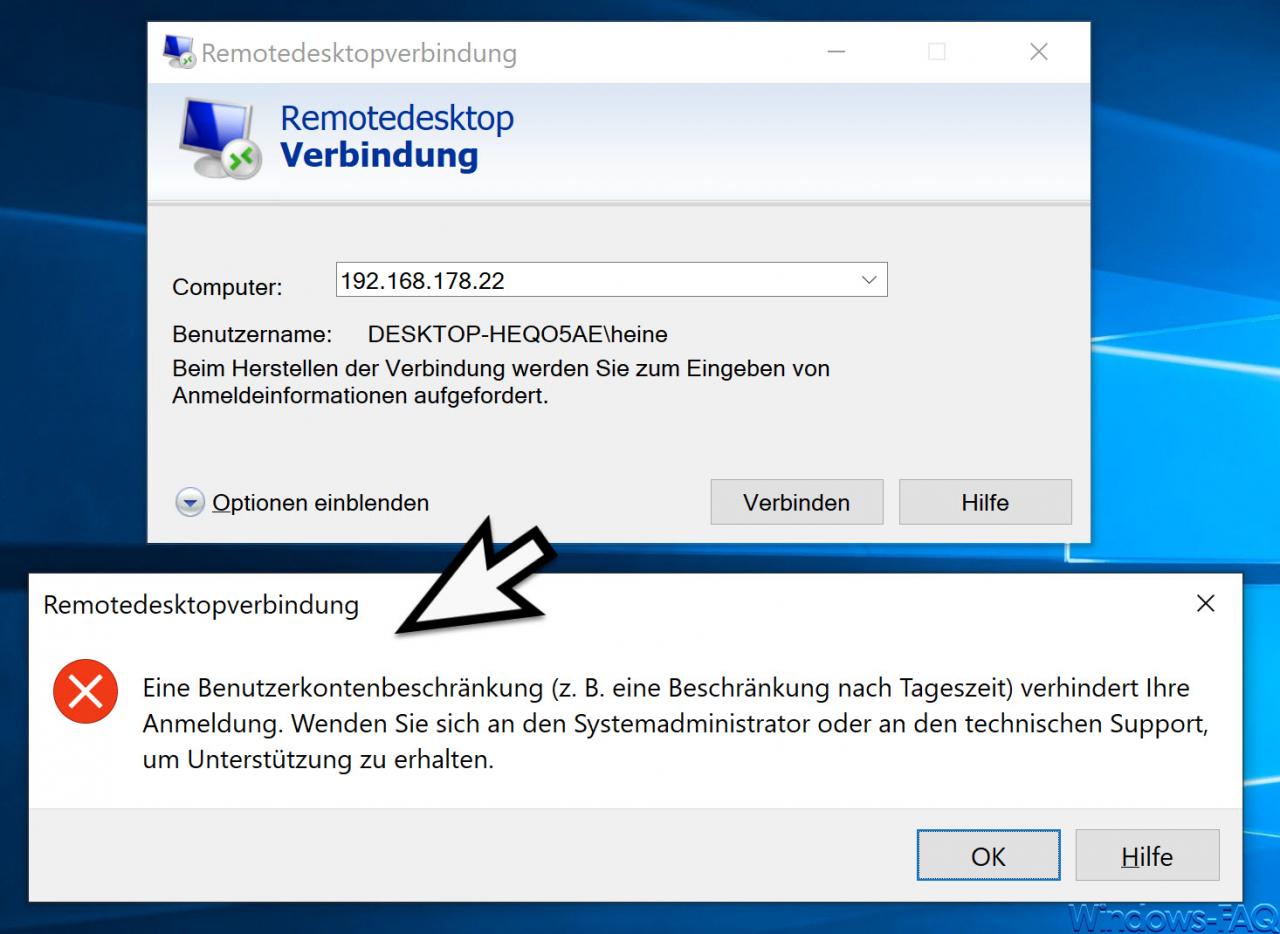
When trying to establish an RDP connection, the following RDP message may appear.
A user account restriction (e.g. a restriction according to the time of day) prevents your registration. Contact the system administrator or technical support for assistance.
As you can see, we tried to make a remote desktop connection to another Windows 10 client on the same network. Although the login data is correct (computer name username), the RDP connection is rejected with this message.
User accounts without a password
The solution is relatively simple, because it is because the user account of the RDP clients has no password . In this case Microsoft does not establish a remote desktop connection to this client and terminates the RDP connection attempt.
A group policy, which also allows an RDP connection without a password, can help here. To do this, start the group policy editor ” gpedit.msc ” and open the following group policy path .
Computer Configuration / Windows Settings / Security Settings / Security Options
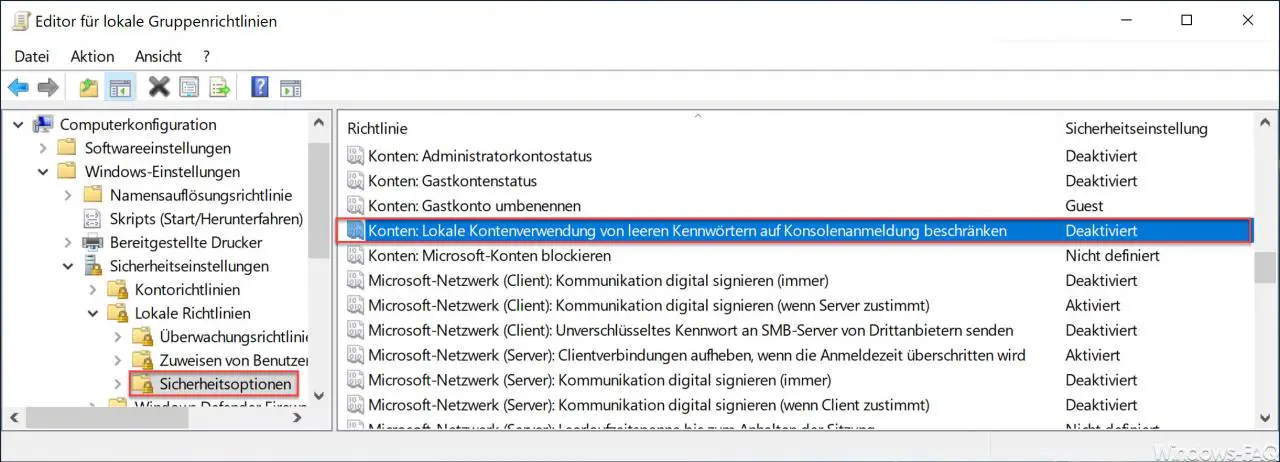
Then there is the GPO, which is ” activated ” by default .
Accounts: Limit local account usage of blank passwords to console login.
Microsoft has released the following information about this RDP GPO.
This security setting determines whether local accounts that are not password-protected can be used to log on from other locations rather than through the physical computer console. When this setting is enabled, users can only log on to the computer console using the non-password-protected local accounts.
Default value: Enabled.
Danger:
Computers that are not in secure locations should always enforce strong password policies for all local user accounts. Otherwise, anyone who sits at the computer can log on to the computer with a user account that is not password-protected. This must be taken into account particularly with portable computers.
If you apply this security policy to the Everyone group, no one can sign in through Remote Desktop Services.
Hints
This setting does not affect logins through domain accounts.
Applications that use interactive remote logons can bypass this setting.
Note: Remote Desktop Services was referred to as Terminal Services in earlier versions of Windows Server.
As soon as you “deactivate” this GPO , you can also connect yourself remotely to another Windows client for which the remote user has no password .
Everyone should of course be aware that user accounts without a password pose a risk and that this GPO should only be deactivated if absolutely necessary.
Should you be interested in further information on the topic of ” Remote Desktop “, please take a look at the following articles.
– Use and provision of virtual desktops (RDP, VDI and DaaS)
– Request RDP information with QWINSTA
– Change standard RDP port 3389
– Close RDP sessions remotely and call up an overview of all RDP sessions with “quser”
– Activate RDP in Windows 10
– Switch off drive redirection
during RDP session – Restart ( shutdown ) PC with Windows 10 during RDP session
– Prevent RDP for local administrators
– Remote desktop connection (RDP) with MSTSC and its parameters
– Activate remote desktop via registry key – Remote desktop
settings now also in Windows 10 Settings app (Fall Creators Update 1709)
– Run CMD prompt remotely via WINRS