We have reported on PowerShell commands several times in the past. Today we would like to show you how you can prepare the PCs in a network so that you can execute PowerShell commands via remote session . This preparation is absolutely necessary, otherwise you will not be able to use the PowerShell remote functions .
The command is responsible for preparation on the target computer
WINRM
WinRM means ” Windows Remote Management ” and it is the Microsoft integration of the network protocol WS-Management ( Web Services Management Protocol ). This Windows service works on the basis of XML and is a protocol which is necessary for remote access . WinRM can not only access WMI functions , it also has the option of accessing the Windows event log. WinRM is the basis for remote access from Windows PowerShell 2.0 .
The WinRM command is extremely extensive with its numerous parameters . However, today we only want to go into the preparation of the Windows client for remote access . To do this, the target computer, which will later be accessed remotely via PowerShell, must be prepared with the following command.
WINRM QUICKCONFIG
Below you can see the execution of the command. It is important that you start the Windows command prompt with administrator rights . Otherwise the changes to the Windows system cannot be made.
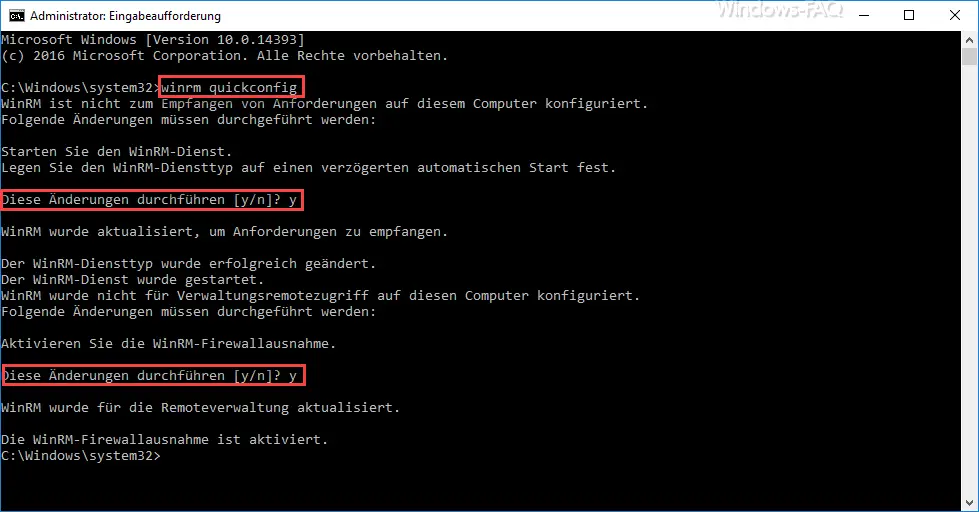
After the command has been started, the following dialog appears
WinRM is not configured to receive requests on this computer.
The following changes must be made:
Start the WinRM service.
Set the WinRM service type to a delayed automatic start.
Make these changes [y / n]? y
WinRM has been updated to receive requests.
The WinRM service type was changed successfully.
The WinRM service was started.
WinRM has not been configured to remotely access this computer.
The following changes must be made:
Activate the WinRM firewall exception.
Make these changes [y / n]? y
WinRM has been updated for remote administration.
The WinRM firewall exception is activated.
As you can see, 2 changes are being made. On the one hand, the WinRM service is now started automatically after restarting the Windows system, but as a delayed start. Secondly, appropriate firewall exceptions are set so that PowerShell remote access works even when the Windows firewall is activated .
All preparations are now made so that you can reach this Windows client via Remote PowerShell . In one of the next posts, we will then take a closer look at the PowerShell remote commands . We have already reported on Windows PowerShell in many other articles, here are the most interesting articles.
– Overview of all PowerShell users & group commands –
Determine Windows system runtime with PowerShell
– Create Windows 10 system restore point with PowerShell
–
Shut down and restart Windows with PowerShell commands – Repair Windows component stores with DISM and PowerShell commands
– UAC (user account control ) via Switch off PowerShell or registry on Windows 10
– PowerShell command to deactivate the firewall