The blocking of USB flash drives is an important feature for many administrators. USB sticks pose a major security risk , especially when used in networks , and are ultimately responsible for injecting viruses, malware or spyware. Unfortunately, many companies handle the dangers and handling of USB sticks too carelessly and trust the employees.
Microsoft provides all the necessary options to prohibit employees from using local USB sticks or to block USB sticks . All that is required is changes in the group guidelines.
Block USB sticks via GPO
In the group policy editor “GPEDIT.MSC” you call the following group policy branch.
Computer configuration / administrative templates / system / removable media access
There are a total of 3 GPOs, which you can set as follows.
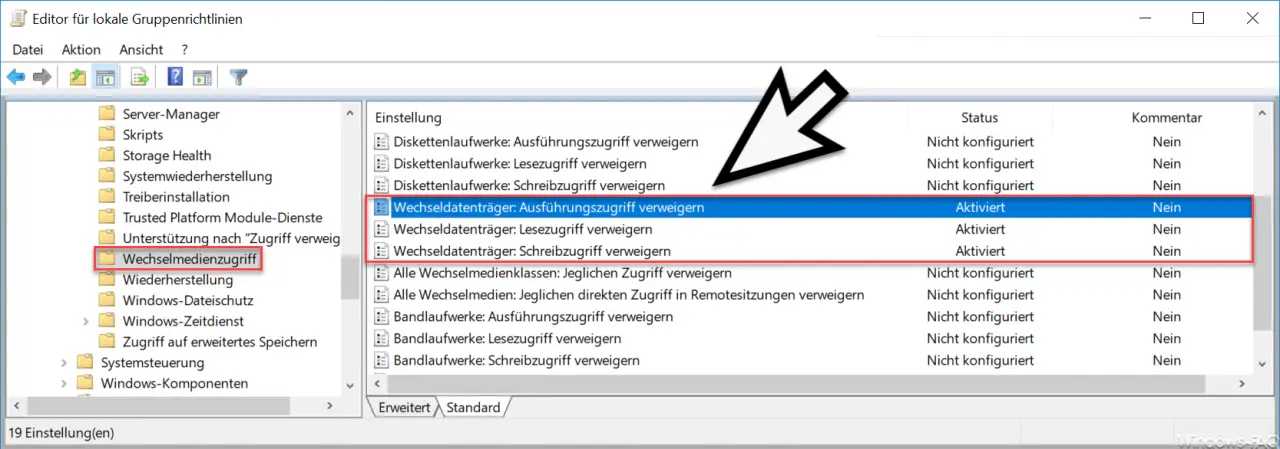
Prevent starting .EXE files from the USB stick
About the GPO
Removable disk: Deny execution access
you can prevent the user from executing “.exe” files directly from the USB data carrier. Microsoft describes the function as follows:
This policy setting denies execution access to removable media.
If you enable this policy setting, execution access to this removable media class is denied.
If you disable or do not configure this policy setting, execution access to this removable media class is allowed.
Block read access to USB stick
About the GPO
Removable disk: Deny read access
you can set that Windows prevents read access to external USB sticks. Microsoft announces the following information.
This policy setting denies read access to removable media.
If you enable this policy setting , read access to this removable media class is denied.
If you disable or do not configure this policy setting, read access to this removable media class is allowed.
Prevent write access to USB sticks
With this group policy you can prevent write access to USB devices.
Removable disk: Deny write access
Microsoft also provides some information about this:
This policy setting denies write access to removable media.
If you enable this policy setting, write access to this removable media class is denied.
If you disable or do not configure this policy setting, write access to this removable media class is allowed.
Note: To write data to users in BitLocker-protected storage, enable the policy setting ” Deny write access to drives not protected with BitLocker “, which is located under “Computer Configuration Administrative Templates Windows Components BitLocker Drive Encryption Removable Data Drives” .
You can find more information on the subject of ” data carriers ” in these articles:
– How can write protection be activated or deactivated on a data carrier
– Convert FAT32 data carrier to NTFS format without data loss
– System repair data carrier / recovery DVD creation under Windows 10
– Backup Exec – SDR data carrier creation – Part 1
– Disk cleanup – Advanced options with Windows 10