The automatic installation of Windows 10 feature updates is a real problem for many companies. The major feature updates such as Windows 10 Anniversary or the Creators Update are simply installed on the Windows 10 clients without prompting . This can have very unpleasant consequences, because not all software used runs immediately with the new Windows 10 feature updates.
Therefore, you should definitely include your Windows 10 PCs in the company environment in ” CBB mode “. This ” Current Branch for Business ” enables you to defer or block these Windows 10 function updates or feature updates for up to 180 days . All you have to do is define a group policy in which you can then specify the number of days for the deferral. You will find the necessary setting under
Reset computer configuration / Administrative templates / Windows components / Windows update / Windows updates
The corresponding option is then called
Select when receiving feature updates
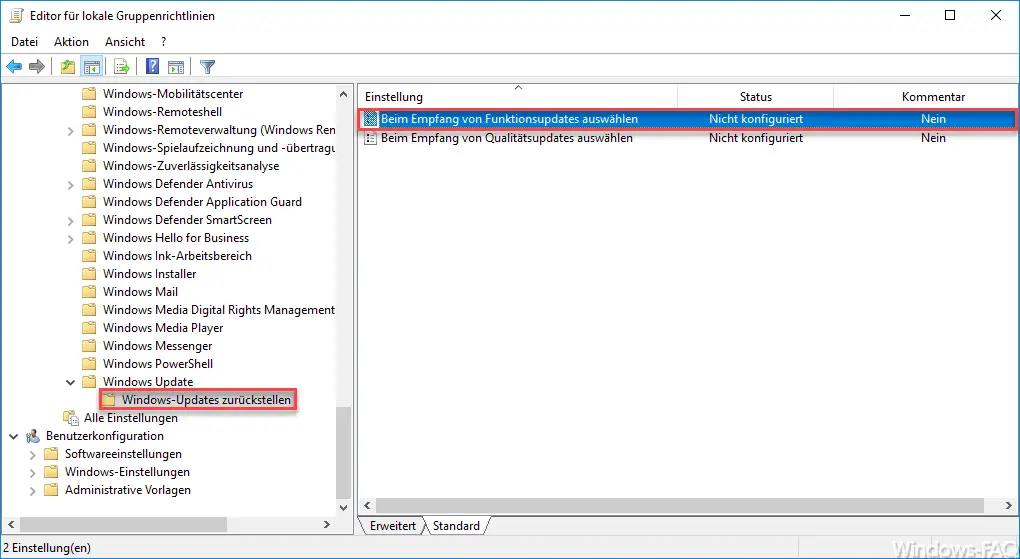
You can then set the following options in this group policy .
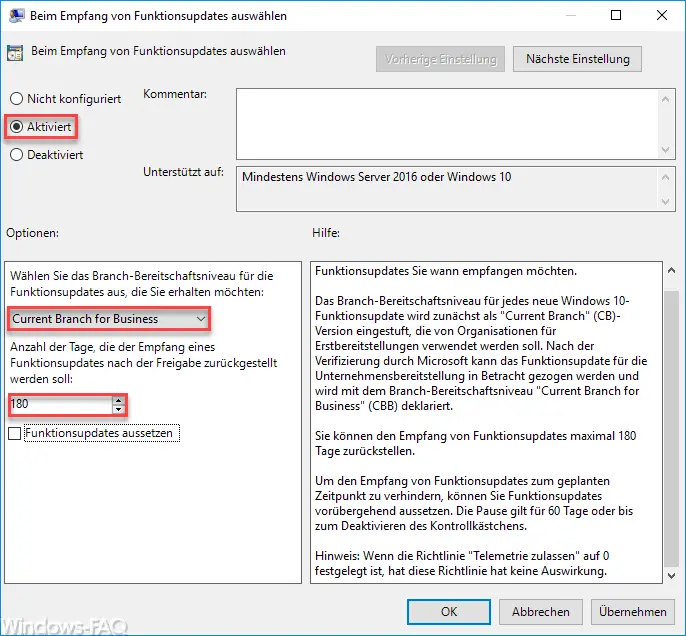
It is important here that you set the ” Branch readiness level ” to ” Current Branch for Business “. With the number of days that you want to postpone the function updates, you can choose between 1 – 180 days. We have selected the maximum period here.
Microsoft explains this group policy as follows:
Check this policy to specify what kind of feature updates you want to receive and when.
The branch readiness level for each new Windows 10 feature update is initially categorized as the “Current Branch” (CB) version that should be used by initial deployment organizations. After verification by Microsoft, the feature update can be considered for enterprise deployment and is declared with the branch readiness level ” Current Branch for Business ” (CBB).
You can postpone receiving functional updates for a maximum of 365 days .
To prevent receiving feature updates at the scheduled time, you can temporarily suspend feature updates. The break lasts for 60 days or until you delete the date from the “Start date” field.
To receive suspended function updates again, delete the date from the ” Start date ” field.
If you disable or do not configure this policy, the behavior of Windows Update will not change.
Note: If the Allow Telemetry policy is set to 0, this policy has no effect.
As you can see from the text, there is even a period of 365 days . Apparently Microsoft has improved here since the Windows 10 Creators Update and increased the deferral days from 180 to 365 days. Furthermore, you can now set a date from which certain function updates can be suspended. You can find this under the option “Suspend function updates from”.
On the Windows 10 clients, it looks like this in the Windows Update settings when the group policy takes effect. The option ” Postpone feature updates ” is greyed out.
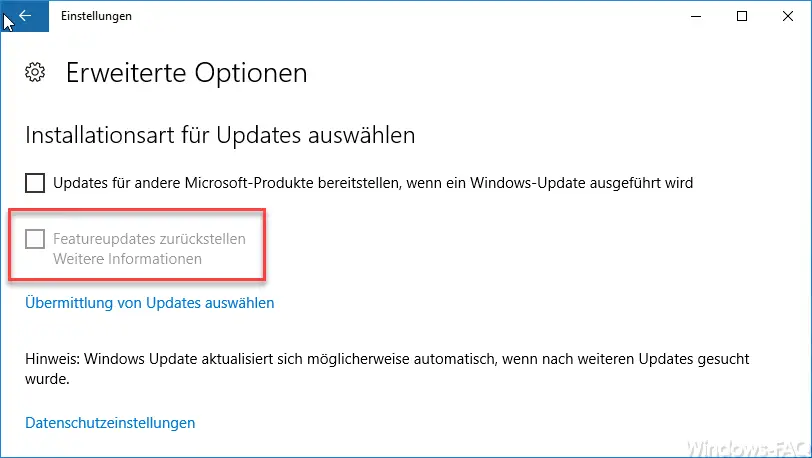
You can activate this setting either as a central group policy via Active Directory or as a local group policy on the Windows 10 clients. Definitely a very important option for us to prevent uncontrolled upgrades of the Windows 10 clients.
If you are interested in other interesting Windows group guidelines, please take a look at the following articles.
– Reset local group policies completely – Deactivate
speech bubbles in Windows 7 (balloon tips)
– Query active group policies with RSOP
– Completely uninstall OneDrive – Windows 10
– Windows 10 folder names and file names greater than 260 characters
– Disable drive redirection during an RDP session
– Prevent RDP for local administrators
– Automatically block Windows after invalid logins
– Switch off Cortana in Windows 10
– Error message 0x8007054b Event ID 15 “Certificate registration …” Eliminate
– Prevent access to Control Panel in Windows 7
– Allow users to only run certain programs