During the regular check of our file server , we noticed that user profiles were stored under the path “C: User” , which actually do not belong there. There were listed names of users who NEVER had the right and had to log on to the file server directly or via remote (RDP) . Nevertheless, the server-stored profiles were there and this was initially absolutely inexplicable. The profiles could not have been created by any tests and they were also very far apart in time, so that I cannot assume a short-term error or problem with the file server .
No other Windows services run on the file server , which could possibly perform a user login and would be responsible for creating a profile . The system is a Windows Server 2008 R2 and has been running without problems for about 3 years. After doing some research on the Internet, I found the problem. Here is a picture of the numerous user profiles on the file server:
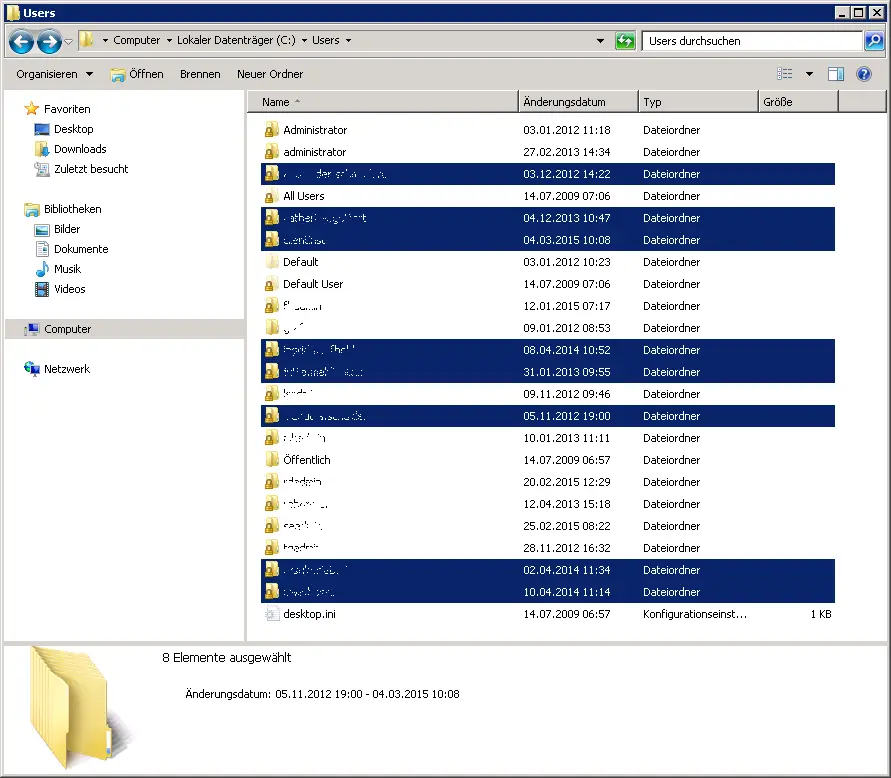
The funny thing was that it wasn’t a specific group of users who used special software, for example. The access rights to the file server directories were also completely different, so that it had nothing to do with it. The solution is somewhere else and the culprit is EFS encryption (Encrypting File System) . The EFS enables users to encrypt confidential file contents. With EFS encryption , the system generates a random key . This key is called FEK (File Encryption Key) . The file or folder to be encrypted is then encrypted with this EFS key and saved together with the file.
This EFS encryption is activated by default on Windows 2008, 2008 R2, 2012 or even 2012 R2 servers and can therefore be used by any user. This works very simply by simply marking the file and folder, switching to the properties and clicking on ” Advanced … “. Here, as can be seen in the following image, there is the item ” Encrypt content to protect data “.
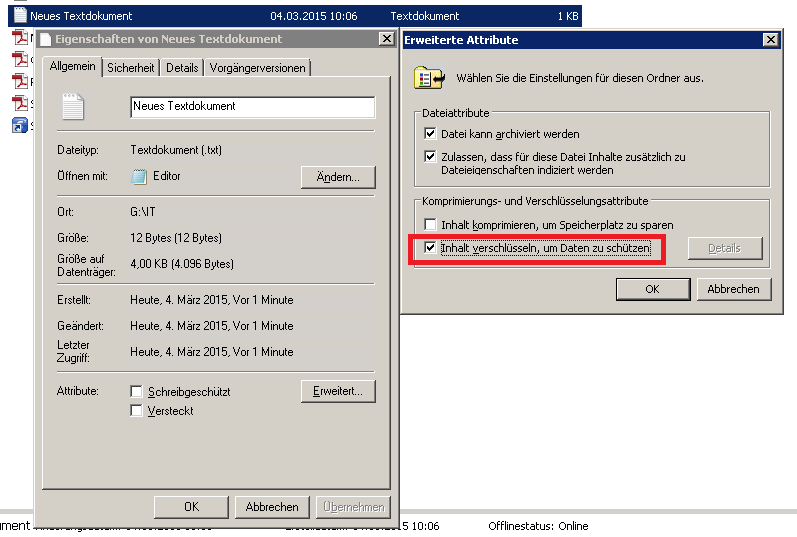
Apparently, the users who now have a server-stored profile on the file server used this option. Whether consciously or unconsciously, the Windows server also creates a local profile in this case . If the admin wants to prevent this, he can only go the way to switch off the EFS . However, the admin should be clear about whether he can really deactivate this feature , not that it will cause other problems. However, the EFS can be deactivated as follows:
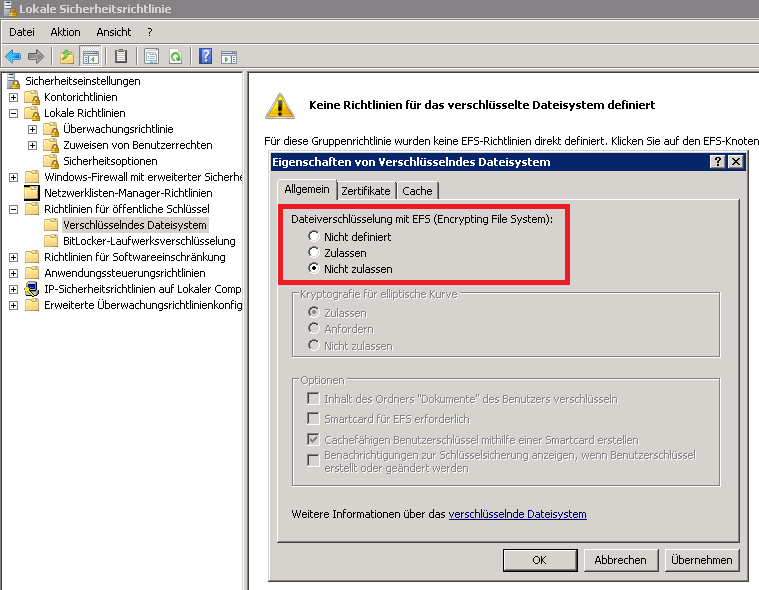
In the local security guidelines you will find under security settings, guidelines for public keys . There you go to the properties and set the setting to ” Do not allow “. This means that the EFS is switched off immediately and the server does not have to be restarted. If the user tries again to encrypt a file or folder , he receives the message ” File encryption is deactivated on this computer “.
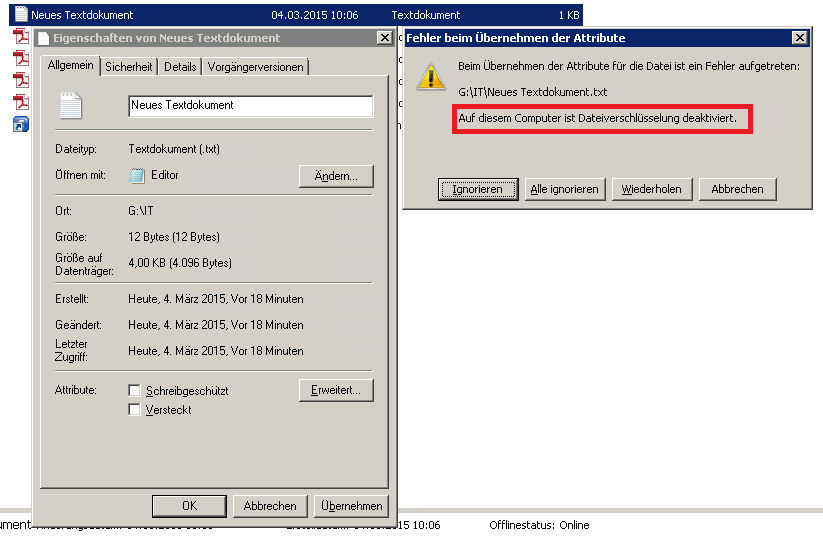
This means that local profiles are no longer generated on the file server.
If you are interested in other interesting articles about Windows Profile , please have a look at the following reports here on Windows FAQ.
– Administrator access to .V2 Profile
– Profile error message “You were logged in with a temporary profile.”
– Roaming Profiles versions – .V6 since Windows 10 Anniversary
– Windows Profile error message “The registration of the service” User Profile Service “failed.”
– Copy profile directories without authorization
– Folder redirection – Profile problems after server failure
– Profiles and system policy problems with the help of Windows log files
– The registration of the service “User
Profile Service” failed – Set security permissions of roaming profile directories correctly