SMBv1 means ” Server Message Block Version 1 ” and is used by Windows 10 to communicate with older network devices. Since SMBv1 is a very old and insecure communication protocol, the WannaCrypt attack showed some time ago. For this reason, anyone who does not necessarily need this SMBv1 protocol should deactivate it.
Disable SMBv1 via PowerShell
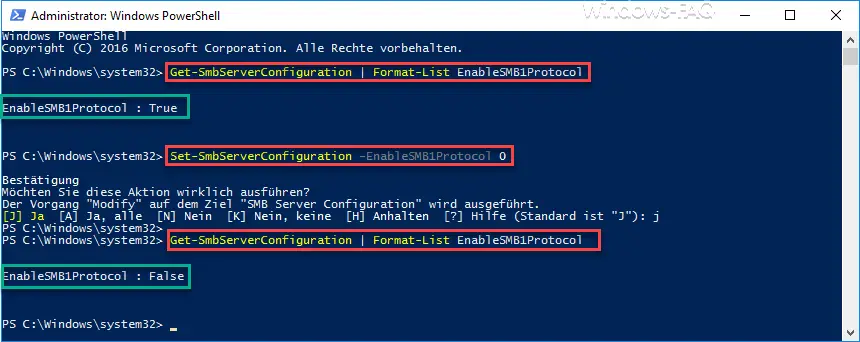
It is easiest to switch the SMBv1 protocol off or on using the PowerShell command . With the following command you can check whether SMBv1 is still active on your Windows 10 system.
Get-SmbServerConfiguration | Format list EnableSMB1Protocol
If you get a ” True ” back, the SMB1 protocol is still active. With ” False ” it is already deactivated and you do not have to do anything else.
ATTENTION: Microsoft has already reacted to the known security vulnerabilities in SMBv1 and automatically switches the protocol off with Windows 10 Fall Creators Update Version 1709. This means that users who are already using the Fall Creators Update do not need to do anything.
If the SMBv1 protocol is still active for you, you can deactivate this with the following command.
Set-SmbServerConfiguration -EnableSMB1Protocol 0
Below we have shown you the entire process in the PowerShell console with the SMBv1 query and the SMBv1 deactivation .
Deactivate SMBv1 via registry
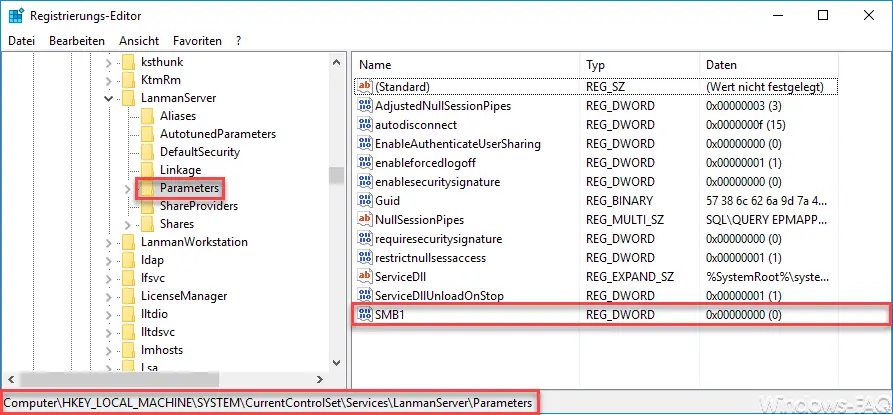
Of course, it is also possible to deactivate SMBv1 using the registry. The following registry key must be called up for this
HKEY_LOCAL_MACHINE SYSTEM CurrentControlSet Services LanmanServer Parameters
There you have to create a new 32-bit DWORD with the following name.
SMB1
This value ” SMB1 ” is the value ” 0 assign”. However, this registry change only becomes active with the next Windows 10 restart.
Below we have listed a few articles that deal with ” protocols “.
– Log Internet activities of the Windows PC’s
– Windows event ID 100 in the event log – Event log
(Eventlog) delete entries quickly using Powershell
– Determine network problems
– Log only ping dropouts – Pingtest.bat – Generate your own event messages in the event log – Switch
off logging of events in the event log
– Robocopy – Missing rights to manage audit logs