Perhaps you have already had the problem that the Windows Firewall was activated on a client in the network for unknown reasons and you therefore no longer have access to the administrative shares C $ or to printer releases. However, this is generally not a problem if you configure a corresponding GPO that allows the incoming exception for file and printer releases.
You can find this corresponding group policy in the following GPO path:
Computer Configuration / Administrative Templates / Network / Network Connections / Windows Defender Firewall / Domain Profile
Here is the following group policy
Windows Defender Firewall: Allow incoming exception for file and printer sharing
Below we have shown you this GPO accordingly.
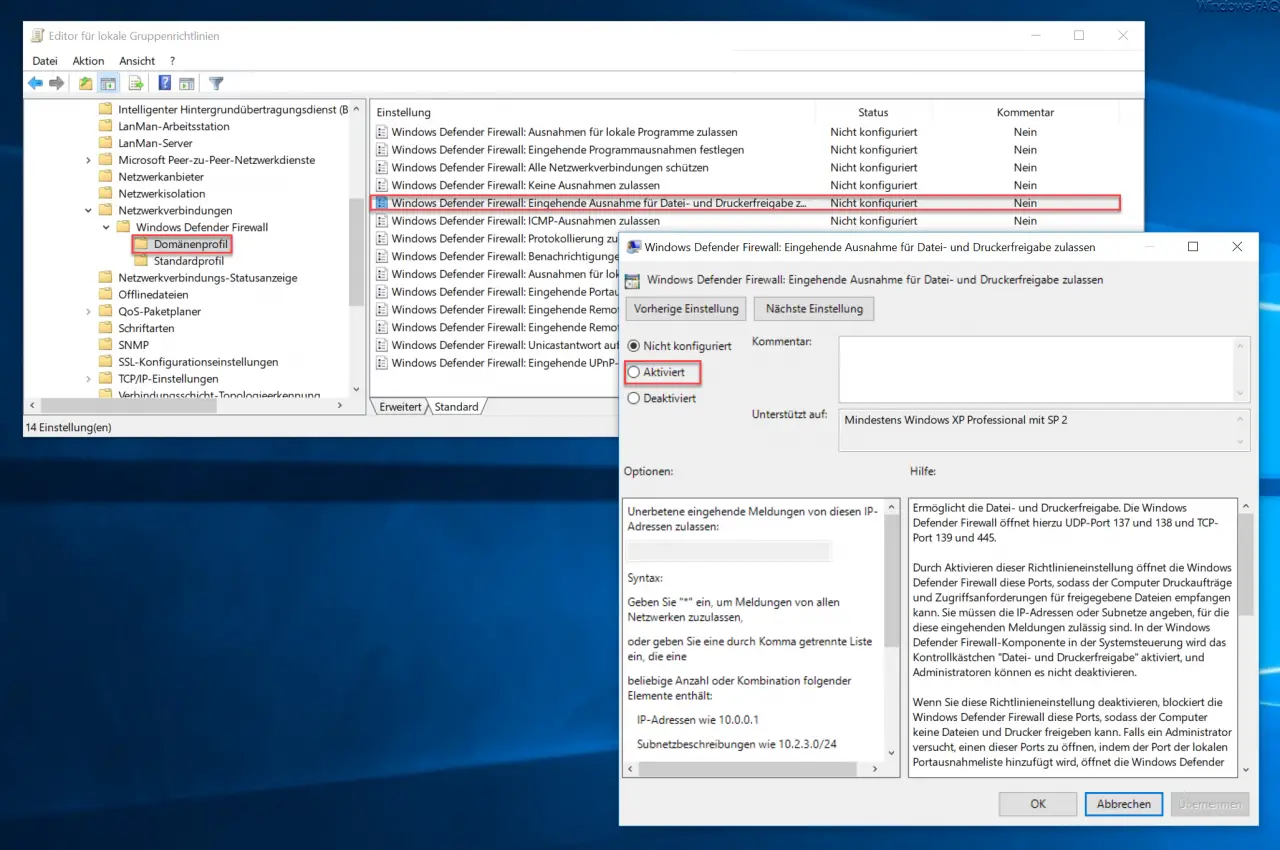
If you now activate this GPO, the Windows file and printer sharing on UDP port 137 and 138 and on TCP port 139 and 445 will be activated despite the active Windows firewall . Microsoft has released the following information about this Group Policy.
By enabling this policy setting, Windows Defender Firewall opens these ports so that the computer can receive print jobs and access requests for shared files. You must specify the IP addresses or subnets for which these incoming messages are permitted. In the Windows Defender Firewall component in the Control Panel, the ” File and Printer Sharing ” check box is selected and administrators cannot deactivate it.
If you disable this policy setting , Windows Defender Firewall will block these ports so that the computer cannot share files and printers. If an administrator tries to open one of these ports by adding the port to the local port exception list, Windows Defender Firewall will not open that port. In this case, the File and Printer Sharing check box in the Windows Defender Firewall component in Control Panel is disabled and administrators cannot select it.
If you do not configure this policy setting, Windows Defender Firewall will not open these ports. Therefore, the computer cannot share files or printers unless an administrator uses different policy settings to open the required ports. In the Windows Defender Firewall component in Control Panel, the “File and Printer Sharing” check box is cleared, but administrators can enable it.
Note: If another policy setting opens TCP port 445, Windows Defender Firewall will allow incoming ICMP echo requests (a message sent by the Ping utility), even if the Windows Defender Firewall: Allow ICMP Exceptions policy setting does would block. The policy settings that TCP port 445 can open include the policy settings “Windows Defender Firewall: Allow Incoming Exception for File and Printer Sharing”, “Windows Defender Firewall: Allow Incoming Remote Management Exception” and “Windows Defender Firewall: Set Incoming Port Exceptions”.
As you can see in the picture above, there are many other useful GPOs that you can set regarding the Windows Defender Firewall . Among other things, this can provide valuable services for remote access to remote PCs.
If you are interested in other useful group guidelines, you should take a closer look at this information.
– Switch off power throttling in Windows 10 via GPO
– Block Windows 10 app access to the camera
– Remove shutdown icon from the Windows login screen via GPO
– Allow remote desktop connections through a group policy
– Remove CD / DVD burning function from Windows Explorer
– Trash symbol not on the
Show desktop – Thumbs.DB – Deactivate the caching of the image thumbnails in Windows Explorer – Set
Windows power options for screen and standby mode via GPO
– Delete Windows swap file by security policy on shutdown
– Deactivate animation when Windows 10 is logged on for the first time