As we wrote a few days ago, we examined our Windows PC more closely with regard to the Meltdown and Specter security problem. The security check that Microsoft makes available to us as a PowerShell script shows the measures required to close the current security vulnerabilities . We explained exactly how to use this script in the article ” Check PC for Meltdown and Specter Vulnerabilities “.
We then checked a PC that contains a current Windows 10 Version 1709 Fall Creators Update with the latest cumulative update KB4056892 from January 2018 ( build 16299.192 ) with the Microsoft PowerShell script. However, most of the areas there were still marked as ” RED “, so that further measures are required to finally close the meltdown and Specter security vulnerabilities .
Since the PC is a Dell Optiplex 9020, we looked at Dell on the homepage for a BIOS update . Dell already reacted to this security problem in January 2018 and provides BIOS updates for almost all available end devices, which adapt the microcode so that Meltdown and Specter should no longer have a chance .
We then downloaded and installed the Bios version A21 for the Optiplex 9020.
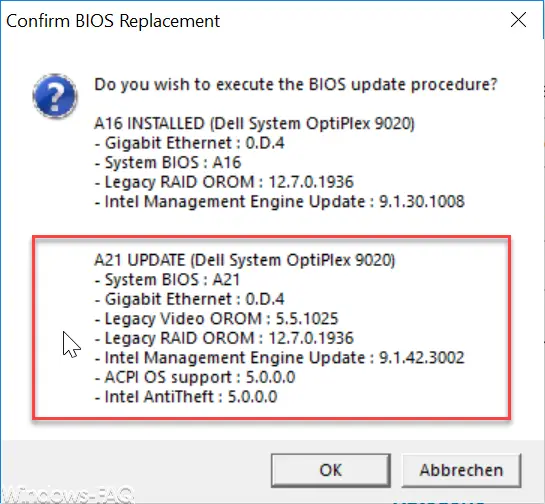
With the bios update we noticed that this process took much longer than with all bios updates before. The PC was also restarted several times during the actual BIOS update process . After a good 5 minutes, the BIOS was updated to version A21 and Windows 10 started up. We then ran the Microsoft Meltdown / Specter test again and found the following.
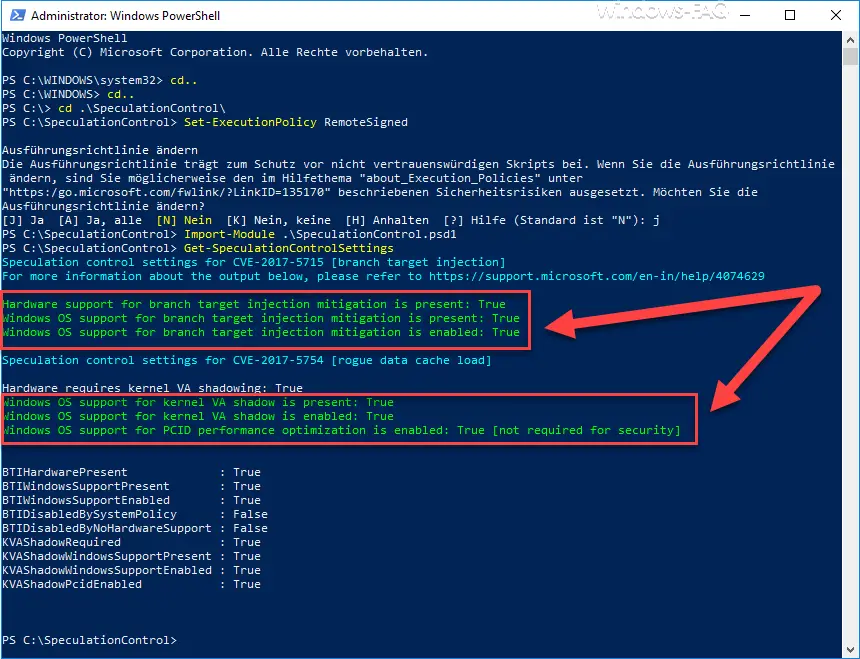
The following is now classified as positive patched:
Speculation control settings for CVE-2017-5715 [branch target injection]
For more information about the output below, please refer to https://support.microsoft.com/en-in/help/4074629
Hardware support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is present: True
Windows OS support for branch target injection mitigation is enabled: True
Speculation control settings for CVE-2017-5754 [rogue data cache load]
Hardware requires kernel VA shadowing: True
Windows OS support for kernel VA shadow is present: True
Windows OS support for kernel VA shadow is enabled: True
Windows OS support for PCID performance optimization is enabled: True [not required for security]
Only after the BIOS renewal were all errors identified previously assessed as OK. It is therefore certain that the meltdown and specter protection is only complete if you have also installed an updated BIOS update . The best thing to do is contact the manufacturer of your hardware for a possible new BIOS version and install it immediately.
For networks that have several hundred or thousands of PCs , this is of course more than annoying. In any case, the IT departments have a good deal of time to do with this until they are fully protected against meltdown and specter .
Note from 01/23/2018: Intel has warned against installing the BIOS updates, because the new microcode may cause an unpredictable restart on some systems. Intel is already correcting the error in the microcodes. So wait until Intel has patched the existing problems. We will inform you as soon as further information is available.
In the following article you will find more information on the topic of ” Security “.
– Decrypt encrypted ransomware files again with a tool
– Search ZIP, RAR or CAB files with Windows Defender – TrendMicro OfficeScan upgrade to version 11.0.6496 SP1 for the Fall Creators Update
– Deactivate or deactivate UAC in Windows 10
– Internet activities of the Windows PC log s