A new cumulative update called KB4057142 was also released for the 1607 Anniversary Windows 10 version a few hours ago . This update increases the Windows 10 version number to version 14393.2034 . Microsoft has integrated a very extensive bug fix in this update KB4057142 and the following bug fixes are known.
- The same improvements as for update KB4057144 have been integrated into this update KB4057142 .
- Resolves issues where the list of iSCSI initiator properties devices does not display certain targets.
- Improves compatibility with U.2 NVMe devices , especially in hot add / removal cases.
- Adds compatibility for NGUID and EUI64-ID formats for NVMe devices.
- Address sync issues where backing up large Resilient File System ( ReFS) volumes can result in errors 0xc2 and 7E.
- Addresses an issue in which the UWF file commit adds old data to files in certain scenarios.
- Address issue where access based enumeration may not work as expected in some scenarios after installing KB4015217 or higher. For example, a user can view another user’s folder for which they do not have access rights.
- A problem has previously occurred when AD FS incorrectly displays the Home Realm Discovery (HRD) page when an Identity Provider (IDP) is assigned to a relying party (RP) in an OAuth group. If the RP in the OAuth group is not assigned multiple IDPs, the user will not see the HRD page. Instead, the user is navigated directly to an associated IDP for authentication.
- Addresses issues have been resolved where PKEyAuth-based device authentication in Internet Explorer and Microsoft Edge sometimes fails when AD FS returns a context that exceeds the URL length request limit. Event 364 is logged in the AD FS 2.0 Admin log with the following exception details : ” System.Security.Cryptography.CryptographicException : the signature is not valid. The data could have been manipulated …
- Addresses an issue in AD FS where MSISConext cookies in request headers may exceed the header size limit. This causes authentication errors with the HTTP status code 400: ” Bad Request – Header Too Long “.
- Addresses issues with AD FS creating an MFA Event 1200 log that does not contain UserID information.
- Addresses issues where retrieving the Certificate Revocation List (CRL ) from the Certificate Authority (CA) fails with the Simple Certificate Enrollment Protocol (SCEP). Users see event ID 45 , which states that “NDES the issuer and serial number in the device request cannot match a certificate authority (CA) certificate”.
- Allows IT administrators scientific troubleshooting I / O errors with a comprehensive event log for the transition of the reliability status .
- Provides transparency about the replication status . It represents the state of replication by indicating when:
- The size of the Hyper-V Replica Log (HRL) is increased to the maximum.
- The recovery point objectives (RPO) threshold was violated.
- Addresses an issue that causes the OCSP pinned response to be used until the renewal date even though the certificate has expired if the certificate status protocol (OCSP) renewal date is after the certificate expiration date.
- Resolves the issue of a delay when trying to find new printers .
- Addresses an issue in which users may not be able to change passwords on the remote login screen if the password has expired.
- Address issue where sometimes custom application defaults are not imported using the DISM command .
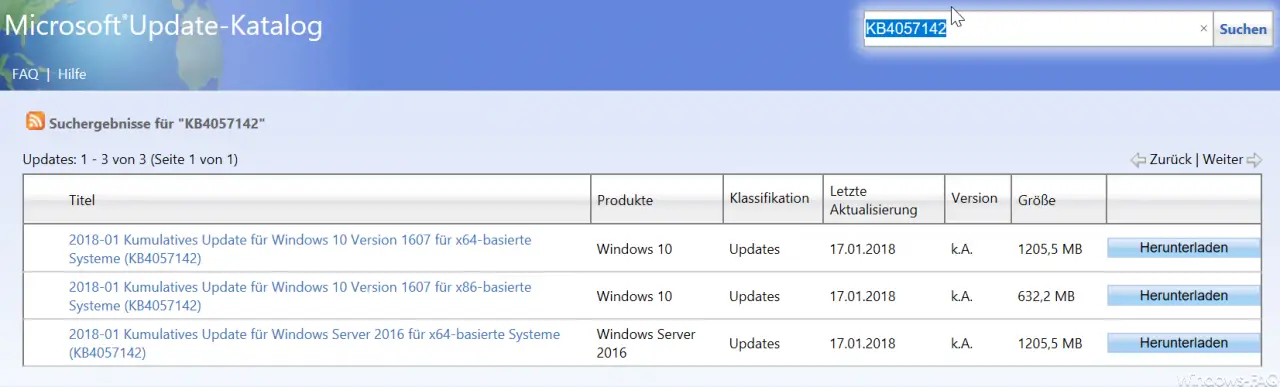
Here you can download the update KB4057142 :
– 2018-01 Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4057142)
– 2018-01 Cumulative Update for Windows 10 Version 1607 for x86-based Systems (KB4057142)
– 2018-01 Cumulative Update for Windows Server 2016 for x64 -based systems (KB4057142)