Due to security gaps, Microsoft made changes in the RDP protocol or in the RDP client and server components some time ago . These changes have been incorporated into numerous Windows security updates that were released in March 2018 . The Fix is a CredSSP vulnerability “remote code execution” (CVE-2018-0886) and is classified as a serious security breach.
In unngepatchten Windows installation CredSSP is a vulnerability remote code execution. An attacker who successfully exploited this CredSSP vulnerability could use the user’s Windows credentials to run malicious code on the target system. Applications that rely on CredSSP for authentication may be vulnerable to this type of attack.
For this reason, it can now happen that you receive the following message in the case of differently patched Windows systems when establishing remote desktop connections (RDP connections).
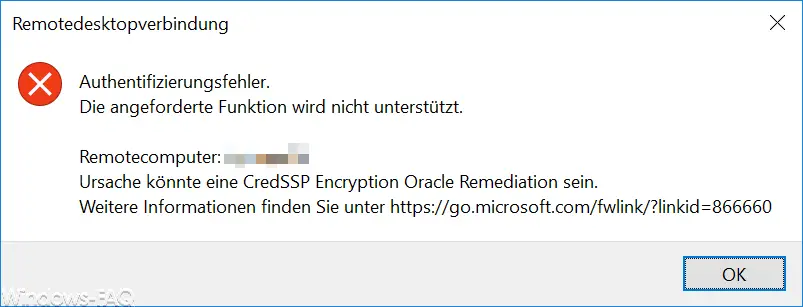
The exact error message is:
Authentication error
The requested function is not supported.
Remote computer: COMPUTERNAME
Cause could be a CredSSP Encryption Oracle Remediation.
Further information can be found at https://go.microsoft.com/fwlink/?=linkid=866660
You now have several options for bypassing or eliminating this message.
Update RDP to the latest status
It certainly makes the most sense to patch the Windows systems in question and thus bring them up to the latest RDP standard. Microsoft has written a fairly comprehensive article, in which you can also find the individual RDP updates for the respective operating systems and there are the appropriate download links for the RDP patches.
You can find the right article under ” CredSSP Encryption Oracle Remediation” Error with a Windows VM in Azure RDP “directly from Microsoft.
We tried this with a Windows Server 2012 R2 and installed the appropriate update KB4103715 (only security update). After restarting the Windows server, the RDP client connection problem was eliminated.
Enable RDP access via registry change
The second possibility is that you make a registry change on the client so that this “encryption Oracle remediation” check is not carried out. The easiest way to do this is to issue the following command from the command prompt.
REG ADD HKLM Software Microsoft Windows CurrentVersion Policies System CredSSP Parameters / v AllowEncryptionOracle / t REG_DWORD / d 2
This command adds the “AllowEncryptionOracle” value to the Windows registry and sets the value to “2”. Thus, the above RDP error message should no longer occur. However, you should still update your system to the current RDP version as soon as possible.
Encryption Oracle Remediation Group Policy
The third option is to set a group policy. You can find the suitable GPO at
Computer configuration / administrative templates / system / delegation of credentials
The group directive is called
Encryption Oracle Remediation (remedy against encryption oracles)
Below you can see this in the “Editor for local group guidelines”.
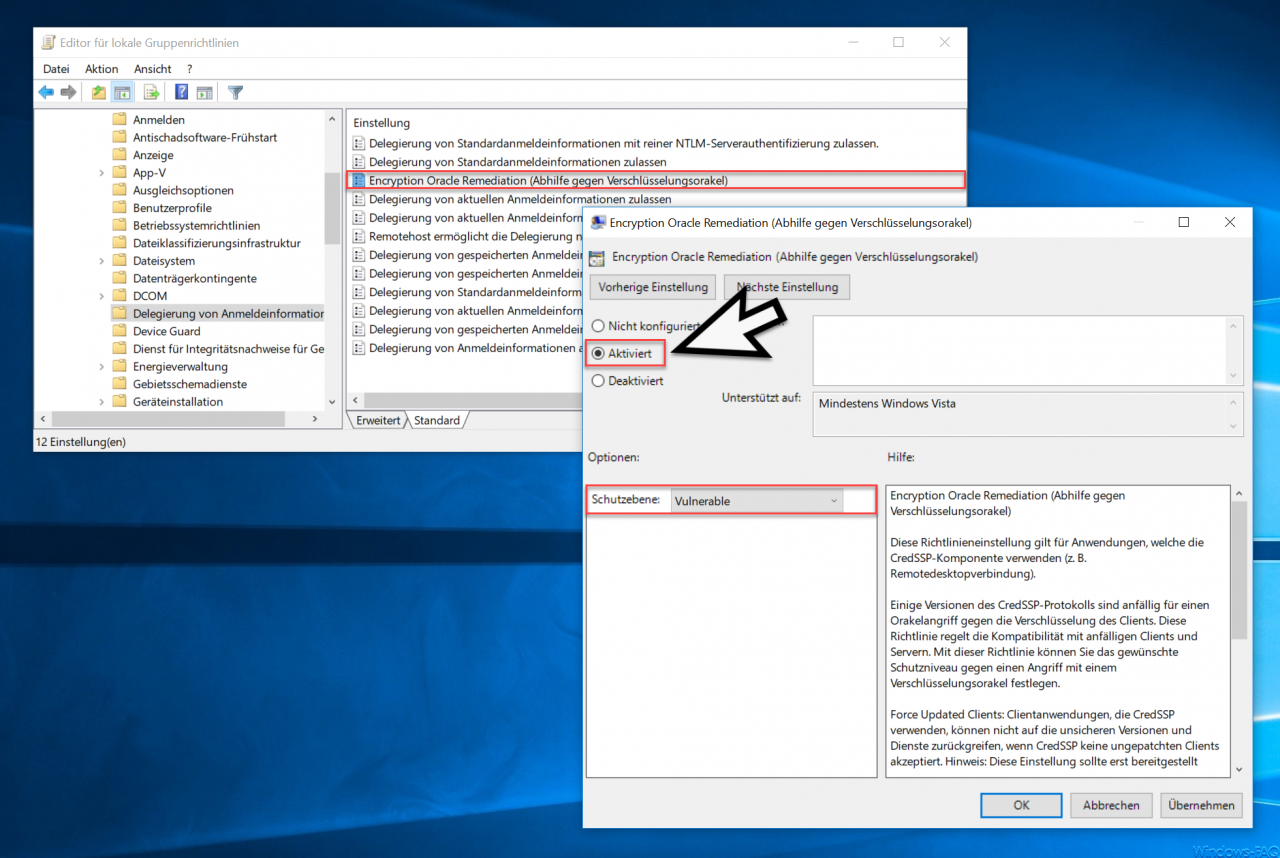
You must now “activate” this GPO and set the protection level as follows.
Protection level: Vulnerable
Microsoft announces further information on this GPO:
This policy setting applies to applications that use the CredSSP component (e.g. Remote Desktop Connection).
Some versions of the CredSSP protocol are vulnerable to an oracle attack against client encryption. This policy governs compatibility with vulnerable clients and servers. This policy allows you to set the level of protection you want against an attack with an encryption oracle.
Force Updated Clients: Client applications that use CredSSP cannot use the insecure versions and services if CredSSP does not accept unpatched clients. Note: This setting should not be deployed until all remote hosts support the latest version.
Mitigated: Client applications that use CredSSP cannot fall back on the insecure version, but services that use CredSSP accept unpatched clients. Under the link below you will find important information about the risk posed by unpatched clients.
Vulnerable: Client applications that use CredSSP expose remote servers to attacks by supporting the use of unsafe versions, and services that use CredSSP accept unpatched clients.
For more information about the vulnerabilities and required safeguards, see https://go.microsoft.com/fwlink/?linkid=866660.
Here, too, however, we recommend that you update your Windows systems to the current patch level and that these RDP connection problems cannot occur at all.
You can find further information on the subject of “RDP” in this article:
– Activate RDP in Windows 10
– Remote desktop connection (RDP) with MSTSC and its parameters
– Switch off drive redirection during RDP session
– Restart ( shutdown ) PC with Windows 10 during RDP session
– Prevent RDP for local administrators